The rapid advancement of technology and the expansion of both hybrid and remote work brings new opportunities to individuals, communities, and organizations. These changes have put organizations at risk of cyberattacks. Malware, phishing attacks, stolen credentials, user error, devices lacking security updates, and physical attacks on stolen devices are major concerns for IT and security teams to protect their workforce.
According to the Microsoft commissioned Security Signals report, 75 percent of security decision-makers feel that the shift to hybrid work puts organizations at risk and makes them vulnerable to security threats.
However, Microsoft provides security to their customers and helps them get secure. With over 1 billion dollars invested in security every year, more than 3500 dedicated security experts and around 1.3 billion Windows 10 devices, Microsoft has deep insights into the security threats faced by their customers.
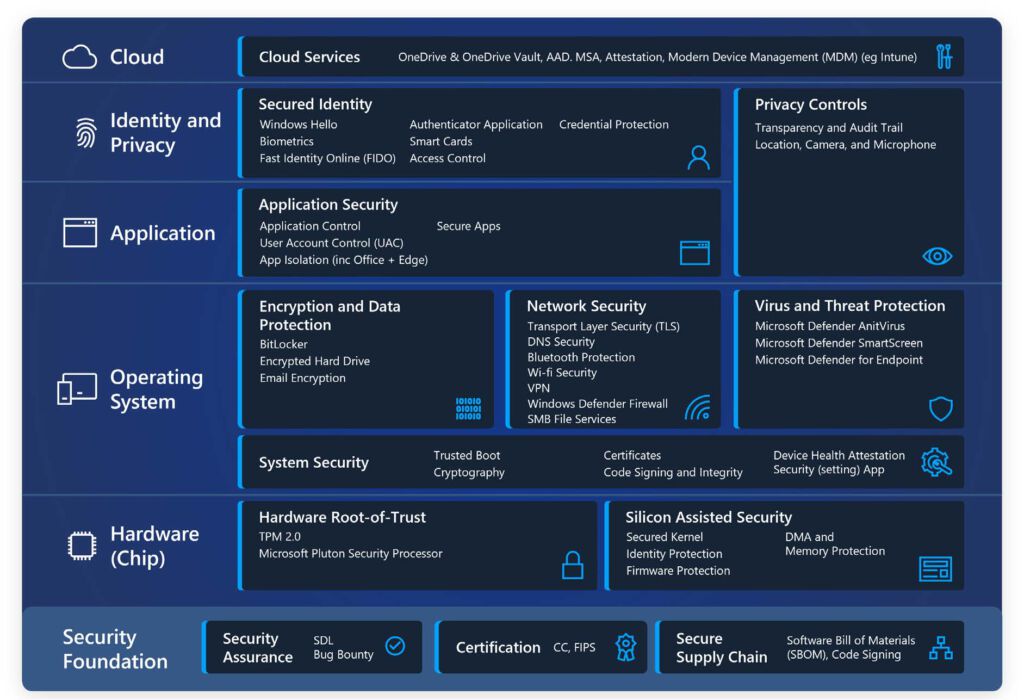
Microsoft Windows 11 comes with Zero Trust principles for the hybrid work environment. This article will explain Microsoft Windows 11 new security features for hardware and cloud services.
Windows 11 Implement Zero Trust Architecture
Zero Trust is a strategic cybersecurity approach that helps secure organizations by eliminating implicit trust and validating each stage of digital interaction. This architecture’s roots are based on the ‘never trust, always verify’ principle.
The zero trust model enables digital transformation and protects the modern environment by leveraging network segmentation, robust authentication methods, preventing lateral movement, and providing layer 7 cyber threat prevention.
Microsoft enabled the zero trust principle, which is threefold.
- Verify explicitly
- Use least privileged access
- Assume breach
First of all, verify explicitly. It means always authenticating and authorizing based on all available data points, such as user identity, device health, location, data classification, service or workload, and anomalies.
The second leverages the least privileged access that limits user access with just-enough-access, just-in-time data protection, and risk-based adaptive policies to secure data and productivity.
Lastly, assume a breach that operates in a manner that reduces segment access and blast radius. Use analytics and verify end-to-end encryption to gain visibility for improving threat detection and defenses.
For Windows 11, verify explicitly applies to the risks introduced by both users and devices. Windows 11 enables chip-to-cloud security, providing IT administrators with the measurements and attestations to determine if a device meets all the security requirements and can be trusted or not. Access decision and enforcement are seamless as Windows 11 works with Azure Active Directory and Microsoft Intune.
Users also benefit from the robust protection measures, including new standards for passwordless protection and hardware-based security. They can replace risky and weak passwords by signing in with a fingerprint or face, a verification code or a security key sent to an email or phone.
Apart from implementing zero trust architecture, Microsoft has focused on hardware and cloud services security as well.
Hardware Security
Advanced threats require advanced solutions with a strong alignment between the hardware and software security techniques. The operating system alone can’t protect from various tools and techniques intruders use to compromise a system. Microsoft has raised the hardware security bar with Windows 11 to design the most secure Windows version.
Windows 11 delivers built-in hardware protection with a powerful combination of hardware root-of-trust and silicon-assisted security.
Hardware Root-of-Trust
It helps to protect and maintain the system integrity as tha hardware turns on, loads the firmware, and launches the operating system Hardware root-of-trust securely measures the operating system and firmware code, boosting the system so that the malware targeting boot code can be detected easily by the operating system and connected services that implement zero trust.
Moreover, it provides a highly secure area deserted from the application and operating system for storing cryptographic keys, data, and code.
1. Trusted Platform Module
A TPM is a firmware root-of-trust designed to offer hardware-based security functions and prevent unwanted tampering. It provides privacy and security benefits to platform owners, system hardware, and users. BitLocker, Windows Hello, Windows Defender System Guard, and various other Windows features rely on the Trusted Platform Module for secure storage, key generation, boot integrity measurements, encryption, and several other capabilities.
2. Pluton Security Technology
It consists of firmware and hardware root-of-trust designed to provide the flexibility and robustness required by advanced PCs to address the rapidly evolving threat landscape. Pluton security design relies on the silicon root-of-trust foundation. It eliminates a common weakness when the root-of-trust is located in a discrete chip on the motherboard separated from the CPU. This flaw exists because the system security depends on the communication path between the CPU and discrete root-of-trust that is often exploitable by physical attacks.
Silicon Assisted Security
Apart from an advanced hardware root-of-trust, there are various other capabilities in the latest CPUs hardening the operating system against threats, such as protecting the memory integrity, safeguarding the boot process, and isolating security-sensitive computers.
1. Secure Kernel
Virtualization-based Security, also known as core isolation, is an essential building block of a secure system. Windows leverages this isolated VBS environment to safeguard security-sensitive OS functions, such as secure kernel and security assets.
Hypervisor-protected Code Integrity (HVCI), also known as memory integrity, utilized VBS to execute Kernel-protected Code Integrity (HVCI) within a secure VBS environment rather than the main Windows kernel. It prevents attacks attempting to modify kernel mode.
2. Windows 11 Secured-core Systems
Secured-core systems strengthen security against advanced threats, such as kernel attacks. These systems help prevent malware attacks and mitigate firmware vulnerabilities by launching into a trusted and clean state at startup. With built-in hypervisor protected code integrity protecting the system memory, secured-core systems ensure that all OS code is trustworthy and approved and known authorities sign all executables.
3. Memory Protection In Secured-core Systems
PCIe hot plugin devices, including USB4, Thunderbolt, and CFexpress, enable users to attach new external peripherals classes. These include graphic cards and other PCI devices. Memory access protection safeguards systems against drive-by DMA attacks using PCIe hotplug devices by restricting the external peripherals from directly copying memory. Secured-core systems defend at the firmware level with several layers of protection.
4. Firmware Protection in Secured-core Systems
Secured-core systems protect at the firmware level with multiple protection layers. It helps ensure that devices start securely in a hardware-controlled state. Sophisticated attacks try to install ‘rootkits’ or ‘bootkits’ to evade detection and get persistence. It’s essential to protect the hypervisor because critical subsystems in Windows use virtualization-based security.
Cloud Services
Data exposure risk has increased with the growth of cloud adoption, the proliferation of existing apps, and increased personal application usage. Windows 11 works with Microsoft cloud services by enabling Zero Trust protection. It helps organizations protect hybrid cloud workloads, strengthen their multi-cloud security infrastructure, and protect sensitive information while mitigating threats.
Protecting Your Work Information
1. Microsoft Azure Active Directory
Azure AD is a cloud identity and access management solution. It’s a leader in the market to manage identities and directories, allowing application access and protecting identities from security threats. Windows work seamlessly with Azure AD to provide identity management, secure access, and single sign-on to applications from anywhere.
2. Modern Device Management
Windows 11 supports modern device management via solutions, such as Intune, to help IT experts manage security policies and business apps while avoiding the risks. Endpoint manager combines Configuration Manager, Microsoft Intune, Windows Autopilot and Desktop Analytics. These services are a part of the Microsoft 365 stack to help protect data, secure access, and manage risks.
3. Remote Wipe
IT administrators might want to wipe data stored in memory or hard disk when a device is stolen or lost. Moreover, a help desk agent might want to reset devices to resolve issues encountered by remote workers.
4. Config Lock
IT administrators implement policies on corporate devices to keep them in a compliant state and safeguard the operating system by preventing users from modifying configurations and creating config drift. It occurs when users with local admin privileges change settings and put the device out of sync with privacy policies. Windows 11 with Config Lock allows IT admins to prevent the config drift and keep the operating system’s configuration in the desired state.